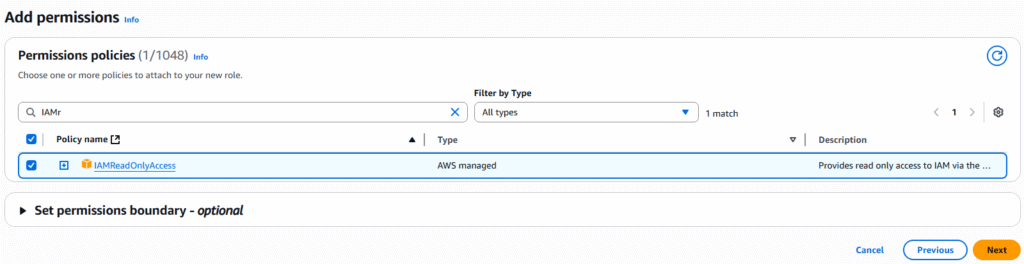
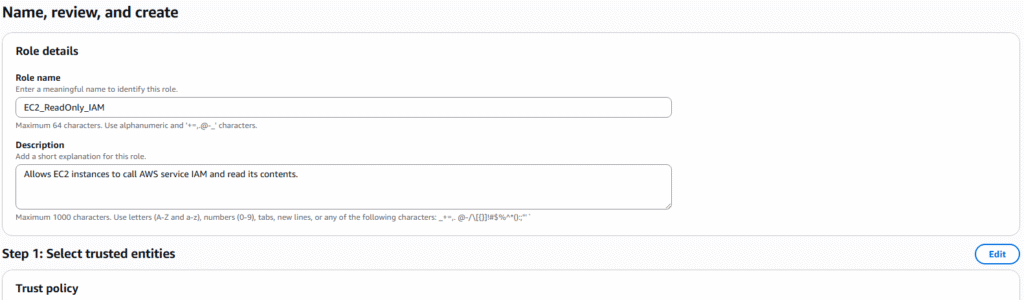
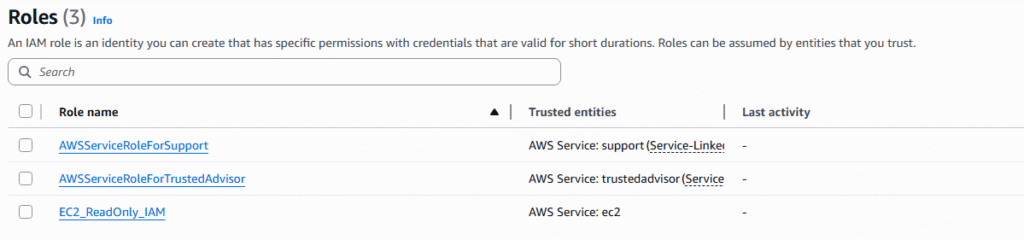
AWS provides security tools in the form of reports and advisors that allow you to see the actions of users and gain knowledge of their behaviors within AWS. We will cover IAM Credentials Reports and IAM Access Advisor.
1. The following is required before you create IAM user for your AWS Free Tier Account.
- An Active AWS Account with admin level permissions..
2. Logon to AWS as an IAM user at URL: https://signin.aws.amazon.com/
3. In the search bar type IAM, highlight the Star next to IAM (So it will appear on you Console) and select IAM.
4. On the left hand side of the screen, scroll down and select Credential reports.
5. Select Download credentials report
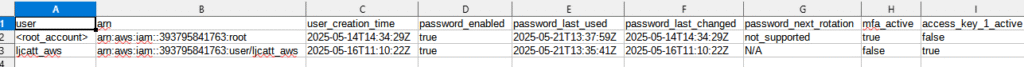
6. A CSV file will be downloaded showing you the activities of each user and other pertenate information about their activities.
7. Now we will go to the IAM Access Advisor. Back on the IAM left hand menu bar select Users.
8. Click on the Users Name you are interested in, this example ljcatt_aws

9. Click on Last Accessed to view the AWS Services used
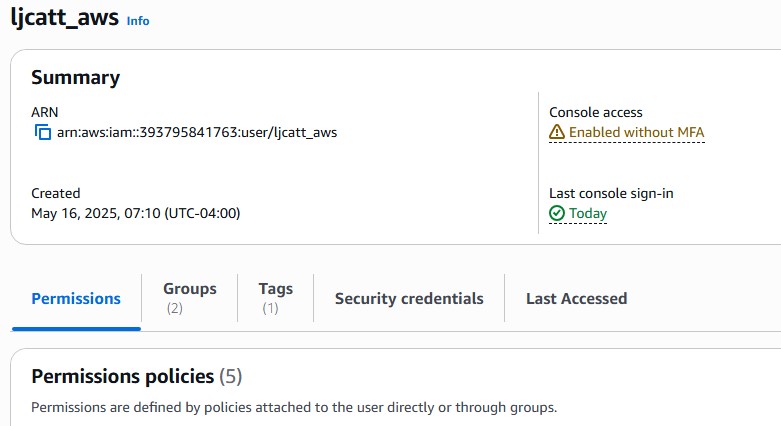
10. You will see the report of services used or not used.